In computing, certain system-level functionalities remain hidden in plain sight—vital for optimal performance, yet overlooked by many users. The A20 menu is one such feature. If you’ve ever interacted with low-level computer architecture, BIOS setup, or legacy system boot processes, the term might sound vaguely familiar. But what exactly is the A20 menu, and why does it matter?
In essence, the A20 menu refers to a system-level configuration interface designed to manage access to the 21st address line—known as the A20 line—within the processor’s memory addressing scheme. This technical mechanism plays a pivotal role in transitioning between real mode and protected mode memory access, critical in operating system boot sequences and compatibility layers.
Though it originated in the context of early IBM PC architecture, its relevance continues in specific embedded systems, legacy support environments, virtualization frameworks, and certain BIOS/UEFI interfaces. This article offers a full-spectrum view of the A20 menu—unpacking its structure, historical significance, practical applications, configuration options, and implications for modern systems.
Introduction to the A20 Line
The A20 line (short for “Address line 20”) is a signal within the x86 CPU architecture, introduced in the 1980s. It allows the processor to address memory beyond the first 1MB barrier—an architectural limit of the Intel 8086 and 8088 processors, which could access only up to 1MB of RAM.
The introduction of the Intel 80286 CPU brought the need for compatibility. The A20 line was implemented to selectively enable or disable access to memory above 1MB, allowing new software to use extended memory while old software remained functional.
Historical Significance of the A20 Gate
The A20 gate was originally controlled via a hardware mechanism, specifically through the keyboard controller (8042 chip). If the A20 line was left active, legacy programs expecting wraparound memory access at the 1MB limit would fail.
To solve this, IBM implemented a gate mechanism—essentially a way to turn the A20 line on or off, depending on software requirements. Over time, the method to toggle the A20 gate became part of bootloaders and operating systems.
This is where the concept of the “A20 menu” begins to evolve.
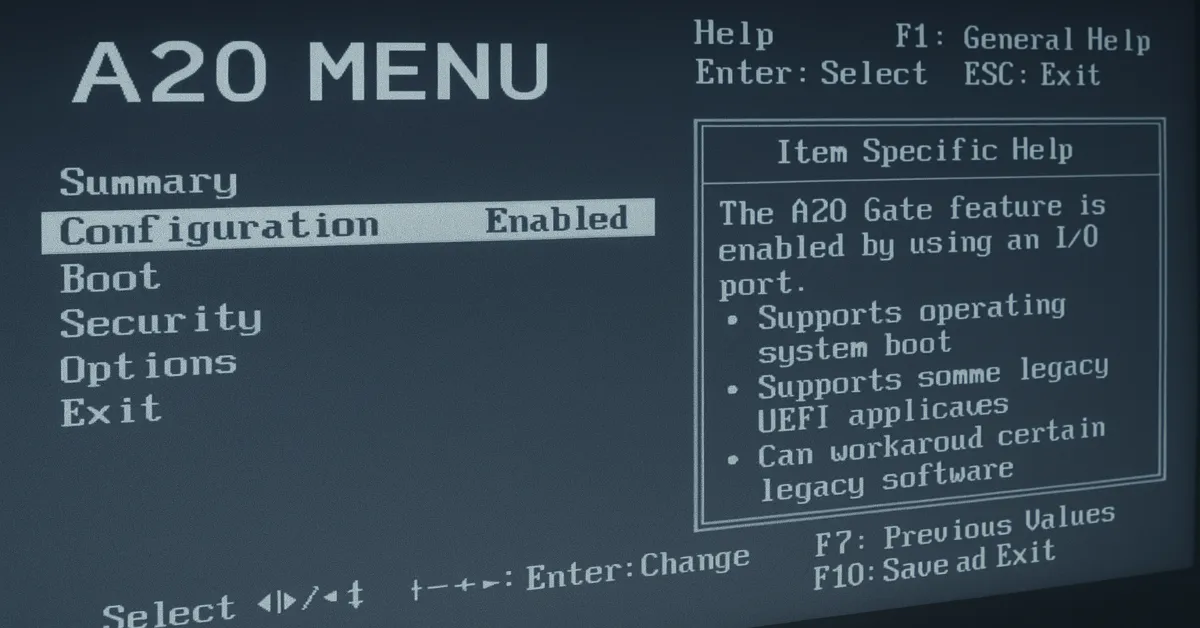
What is the A20 Menu?
The A20 menu is not a menu in the conventional sense seen by end-users on GUIs. Instead, it is a conceptual and sometimes interface-based representation—often found in BIOS, UEFI, and bootloader environments—that manages the behavior of the A20 line.
In essence, it allows developers, system administrators, or BIOS-level configurations to:
- Enable or disable the A20 line
- Set rules for memory access compatibility
- Trigger legacy or modern boot sequences
On certain systems—especially embedded platforms or diagnostic firmware—the A20 menu can present itself as a selectable configuration, with toggle options or automatic detection features.
Why the A20 Menu Still Matters
Despite seeming archaic, the A20 mechanism still has contemporary relevance for a few key reasons:
- Legacy Hardware Support: Many enterprise systems and embedded applications still rely on 16-bit compatibility.
- Bootloader Consistency: Operating systems like Linux and Windows perform A20 gate manipulation during bootup.
- Virtual Machine Emulation: Hypervisors must replicate A20 behavior to accurately model legacy environments.
- Custom Firmware Design: Low-level system designers may use A20 control for system stability or testing.
Technical Structure of the A20 Menu
Here’s a typical structure found in an A20 menu configuration, whether in firmware or boot code:
| Option | Description | Default Behavior |
|---|---|---|
| Enable A20 | Allows memory access above 1MB | Enabled |
| Disable A20 | Emulates legacy memory behavior | Disabled |
| Auto-detect | System toggles based on environment | Enabled if legacy detected |
| A20 Method | Select between chipset, BIOS, or keyboard controller control | Chipset |
These configurations allow highly granular control over how the A20 gate behaves in specific circumstances.
Use Cases in Modern Computing
While most consumer-grade computers auto-configure the A20 line behind the scenes, advanced applications still benefit from explicit A20 menu configurations:
- Operating System Installers: Especially in multi-boot or recovery environments
- Legacy Application Emulators: DOSBox, QEMU, and others emulate A20 behavior
- Embedded Diagnostics: A20 configurations can be used to validate memory wrap behavior
- Firmware Developers: UEFI and coreboot developers may leverage A20 states during early system initialization
BIOS/UEFI Configuration Options
BIOS and UEFI implementations sometimes expose A20 toggles in Advanced Settings or Compatibility Modes. These settings are often labeled as:
- Fast A20 Enable
- Legacy Memory Access
- Extended Memory Access Gate
While newer UEFI implementations automate the A20 decision-making, older BIOS versions still leave it to the system administrator to configure.
A20 Menu and Bootloader Interaction
Bootloaders like GRUB, LILO, or even Windows Boot Manager may engage the A20 gate during startup to shift from real mode to protected mode.
This transition enables the use of high memory addresses and is fundamental for any modern OS. The A20 menu, when exposed, can allow system integrators to ensure this transition occurs smoothly.
Example bootloader behavior:
GRUBcalls A20 enable functions via BIOS interruptsLILOuses inline assembly to manipulate A20 via I/O ports- Custom kernels may use direct A20 toggling during early boot stages
Debugging and Troubleshooting with the A20 Menu
In debugging scenarios—especially on legacy systems—a malfunctioning A20 gate can lead to:
- Unexpected reboots
- Boot failures
- Segmentation errors in memory access
Advanced diagnostics tools may expose the A20 state. Developers can use the A20 menu to isolate whether memory mismanagement is caused by improper A20 toggling.
Security Implications and Access Control
Interestingly, the A20 mechanism has also been explored in the context of security hardening. While not a primary attack vector, improper A20 gate configurations can result in:
- Unauthorized memory access during boot
- Memory leakage between protected and real modes
- Increased vulnerability in systems lacking address verification
Systems using Secure Boot or TPM-based validation now enforce stricter control, including A20 state checks, during the measured boot process.
Virtualization and the A20 Line
Virtual machines—especially those emulating x86 hardware—must replicate A20 behavior accurately to boot legacy operating systems. Hypervisors like VMware, KVM, and Hyper-V simulate A20 toggling within the virtual BIOS layer.
In such contexts, the A20 menu might exist as a configuration flag or be programmatically toggled during VM runtime.
Legacy Software and A20 Compatibility
Old software, particularly those written for DOS, Windows 3.x, or early Linux kernels, relies on precise memory expectations. If the A20 line is erroneously enabled or disabled, software may crash or misbehave.
The A20 menu allows backward compatibility—enabling hybrid environments where modern systems run legacy code.
Industry Applications and Embedded Systems
In industrial controllers, aerospace systems, and medical devices, where embedded systems persist for decades, the A20 menu retains critical value. It ensures:
- Predictable memory behavior
- Extended lifecycle support for old software
- Reliable system booting on custom firmware
Common Myths and Misconceptions
Myth: The A20 gate is obsolete in modern systems.
Fact: It’s automated, not obsolete. It’s still fundamental in boot sequences and legacy support.
Myth: The A20 menu can improve performance.
Fact: It doesn’t affect performance directly, but misconfiguration can hinder boot reliability.
Myth: Only BIOS handles the A20 line.
Fact: It can be controlled by the chipset, keyboard controller, or even OS-level code.
Programming Considerations
For developers writing boot code or kernel modules, handling the A20 line might involve:
asmCopyEdit; Enable A20 via port 0x64
mov al, 0xD1
out 0x64, al
; Wait until ready, then send command
in al, 0x64
cmp al, 0
jne $-1
mov al, 0xDF
out 0x60, al
This snippet shows a low-level method to enable A20 via the keyboard controller. Programmers today wrap this logic in BIOS/UEFI calls.
A20 and 64-bit Architecture
In 64-bit CPUs, memory access far exceeds the 1MB barrier. Still, during initial boot stages, the CPU starts in real mode—just like older chips. The transition path to 64-bit long mode involves enabling the A20 line before paging and segment registers are reconfigured.
So yes, even your modern CPU relies momentarily on A20 logic during boot.
Case Studies
Case Study 1: A defense contractor using 1990s BIOS firmware discovered memory errors after retrofitting with newer RAM. Analysis revealed the A20 gate was disabled, causing legacy wraparound memory bugs.
Case Study 2: An open-source OS failed to boot on certain motherboards. Investigation traced the issue to BIOS that failed to auto-enable A20. Manual toggle in the A20 menu fixed the problem.
Future of the A20 Menu
The A20 line’s manual control may fade, but its logic is immortalized in firmware, virtual environments, and compatibility layers.
Going forward, A20 configuration will likely be abstracted further, but understanding its role remains important for:
- Firmware developers
- Virtualization engineers
- Security researchers
- System architects
Final Thoughts
The A20 menu may appear technical and obscure, but it underscores a fundamental architectural reality: backward compatibility matters. Whether you’re booting a virtual machine, configuring an embedded controller, or writing a kernel, knowing how the A20 line behaves is essential.
Modern systems may hide this complexity, but it persists—just beneath the surface. Understanding the A20 menu is not just about legacy support; it’s about respecting the hidden scaffolding of modern computing.
Knowledge of the A20 menu bridges the past and future—where bits and bytes are not just processed, but understood.
FAQs
1. What exactly does the A20 menu control?
The A20 menu manages the activation of the A20 address line, which determines whether a system can access memory above the 1MB barrier. It’s essential during the system’s transition from real mode to protected mode in early boot stages, ensuring compatibility with both legacy and modern memory access requirements.
2. Is the A20 menu visible in all BIOS or UEFI setups?
No, most modern BIOS/UEFI firmware automatically manages the A20 line behind the scenes. However, in certain advanced or legacy BIOS setups—especially in embedded systems—the A20 menu may be exposed to allow manual control or diagnostics for developers and system integrators.
3. Can disabling the A20 line cause boot failures?
Yes. Disabling the A20 line incorrectly can prevent an operating system from accessing necessary memory, causing boot loops, crashes, or segmentation errors. It’s critical in any system that needs to switch to protected or long mode during boot.
4. Is the A20 menu still relevant on 64-bit systems?
Yes, indirectly. Even 64-bit systems begin execution in real mode and must enable the A20 line before transitioning to protected and then long mode. While users don’t usually interact with it, the logic remains crucial during bootloader and firmware stages.
5. Who needs to understand or use the A20 menu today?
Primarily, the A20 menu is relevant to:
- Firmware developers
- Embedded systems engineers
- Security researchers
- Virtualization architects
- Legacy system maintainers
For most end users, it remains behind-the-scenes, but for system-level professionals, it’s a critical piece of computing history and ongoing functionality.